Office 365 and EWS with OAuth 2.0 authentication in unattended (app-only) mode: How to make it work
On October 1st 2022, Microsoft will begin disabling Basic authentication in Microsoft 365 for EWS, IMAP and POP3. This means that classic username/password authentication will no longer work with Exchange Online, and application will have to be upgraded to use OAuth 2.0.
Microsoft 365 (formerly Office 365) supports two kinds of OAuth 2.0 authentication:
Delegated authentication is suitable for desktop, mobile or web applications with signed-in user present.
This mode is described in detail in another article.App-only authentication is suitable for services or daemons with no user present. Instead, these unattended applications authenticate using client secrets (application credentials) to receive an access token, which is then used to gain access to a mailbox using IMAP, POP3 or EWS protocols.
Before your application can start accessing mailboxes, you have to register it with Microsoft, assign the relevant permissions and configure mailbox access. The guide below describes what needs to be done to enable EWS access for unattended apps (app-only mode). For IMAP or POP3, see Office 365 and IMAP or POP3 with OAuth 2.0 in unattended mode.
Register yourself and your company
Log into Azure Portal. If you don't have an account there yet, create it. You also have to set up a tenant that represents your company.
If you administer more than one tenant, use
Directories + subscriptionsfilter to select the tenant for whom to register an application.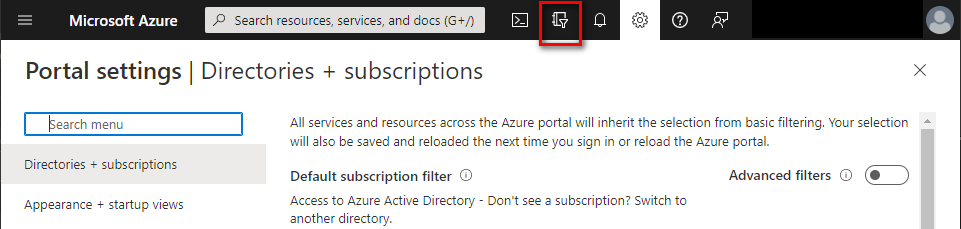
Register your application
In Azure Portal ⇒ expand the left menu ⇒ select
Azure Active Directory⇒ selectApp registrations⇒ click+ New registration. (Azure Portal is constantly evolving, so if you cannot find this page, use the search bar.)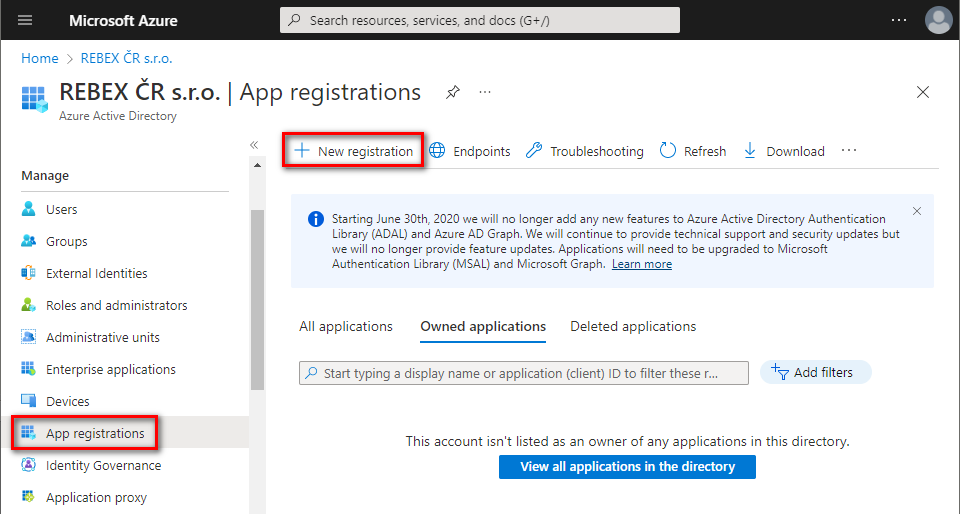
Name your application, choose which kind of accounts are going to use it, and click
Register.Note: This guide is suitable for single tenant account types. For other types, further steps might be different.
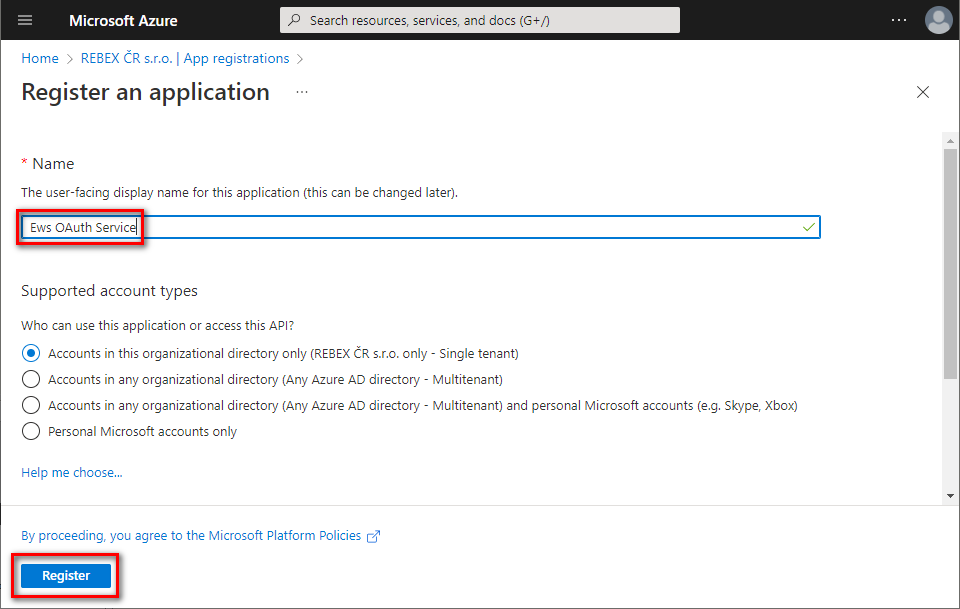
You successfully registered your application and you can view its associated IDs. Some of them will be needed later to obtain an OAuth 2.0 token.
Set up client secret (application password)
In the left menu, select
Certificates & secrets⇒ click+ New client secret.
Provide some description for this secret, choose expiration period, and click
Add.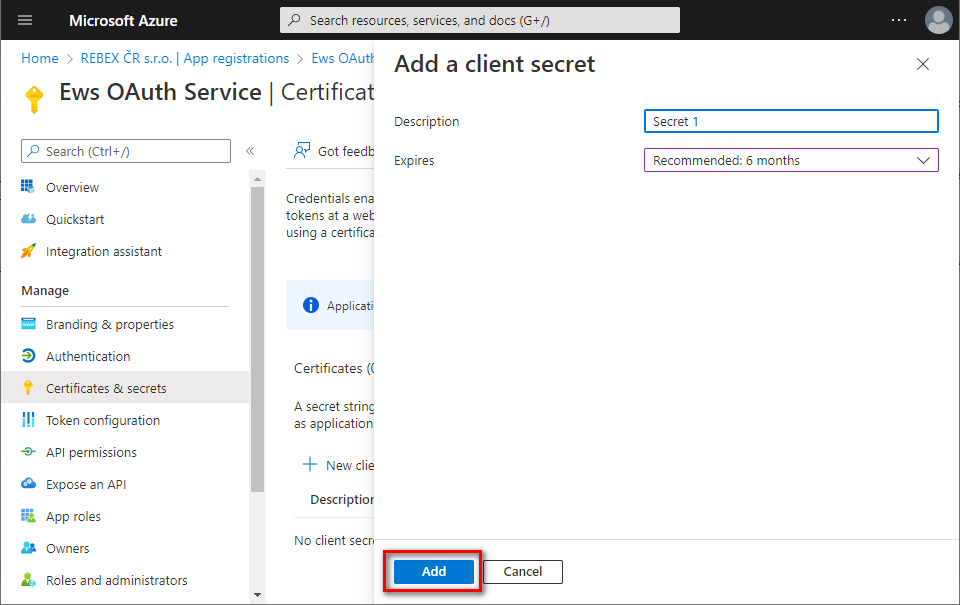
Immediately copy and save the newly created client secret's
Value(notSecret ID). You will not be able to view theValuelater anymore.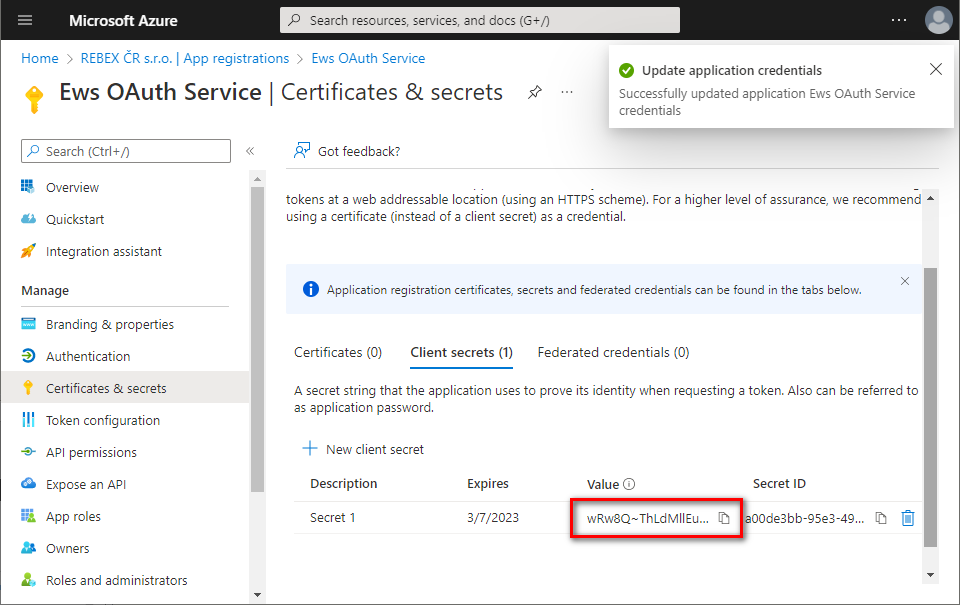
Add app permissions
In the left menu, select
API permissions⇒ click+ Add a permission.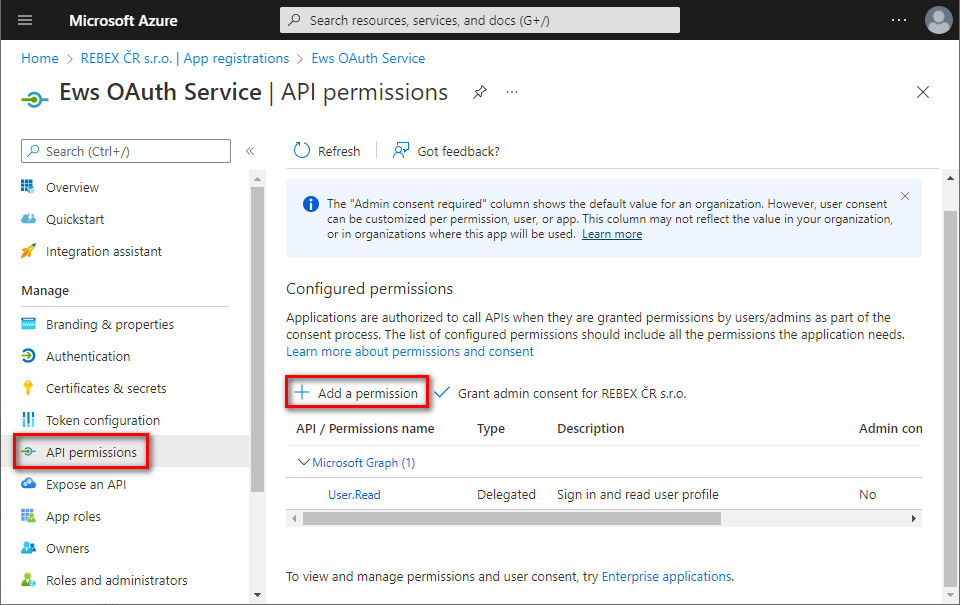
Navigate to
APIs my organization usestab ⇒ typeOffice 365 Exchangein the search bar ⇒ clickOffice 365 Exchange Onlineentry.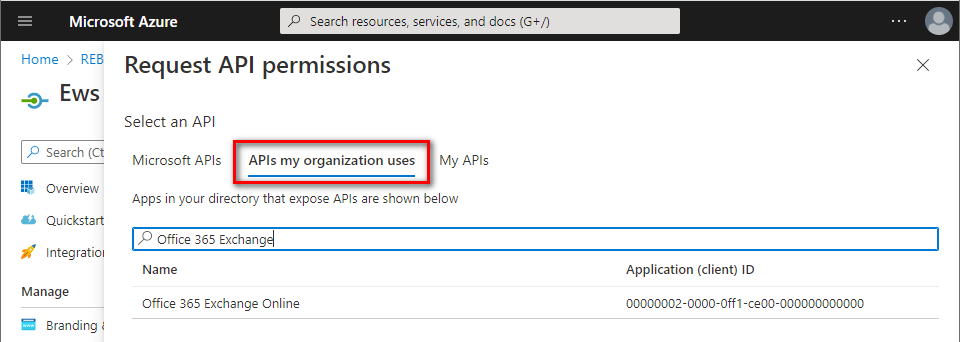
Click
Application permissions⇒ checkfull_access_as_app⇒ clickAdd permissions.Note:
Mail.Read,Mail.ReadWrite,Mail.Sendpermissions are not suitable for EWS.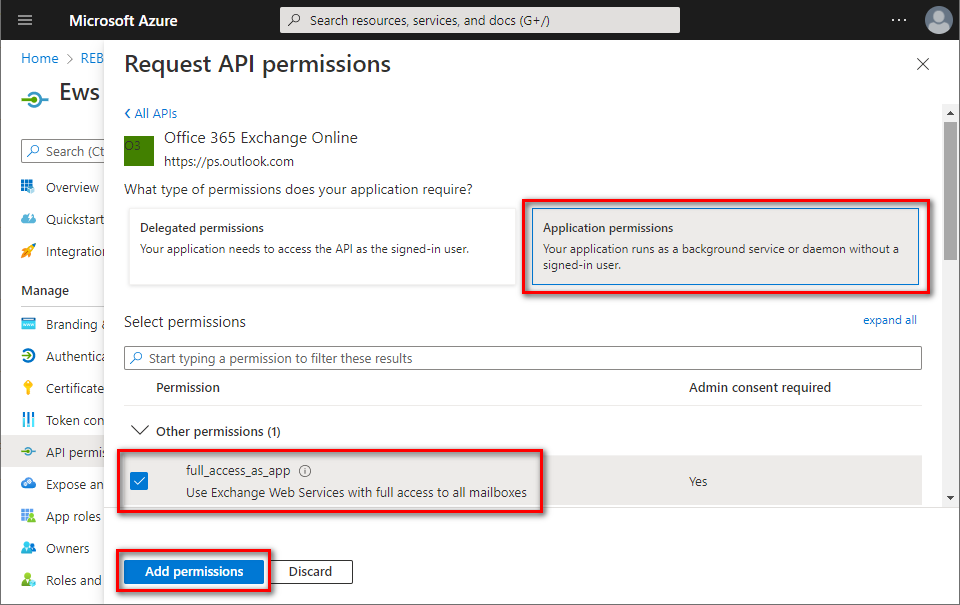
The newly-added
full_access_as_apppermission has to be approved by your organization's administrator. Ask them to grant consent to your application by clickingGrant admin consent for [organization].Note: This grants read-write access to all Exchange Online mailboxes in your organization. To restrict this, read How to restrict mailbox access of Azure applications in app-only mode article.
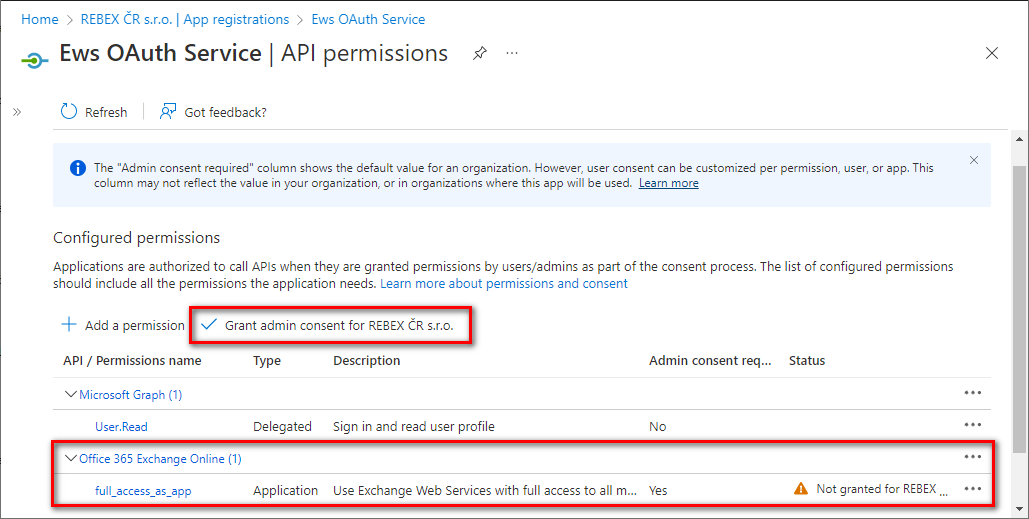
Application permissions have been granted. Optionally, you can remove the delegated
User.Readpermission which is not needed for app-only application - click the context menu on the right side of the permission and selectRemove permission.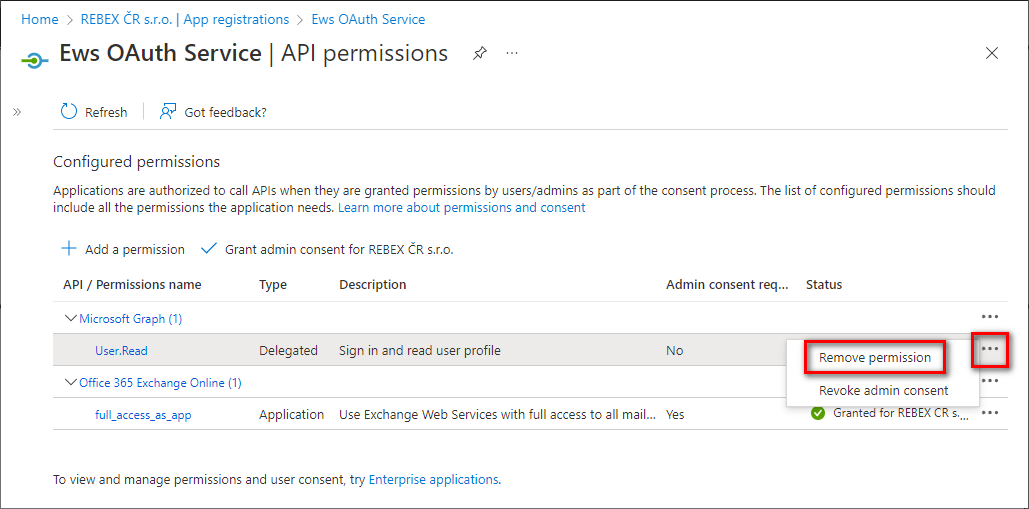
Congratulations! Now you have registered an application for accessing Office 365 mailboxes via EWS protocol and received its
Application (client) ID,Client secretandDirectory (tenant) ID.These strings are going to be used by your application to authenticate to Microsoft 365 via OAuth 2.0 and receive an OAuth token. This token is then used to authenticate to Exchange Online using the EWS protocol.
Let's write some code!
In your application, add reference to Microsoft.Identity.Client package, and specify your IDs, the secret, and the e-mail address. Specify the scope to request a token as well (use
https://outlook.office365.com/.defaultin app-only mode).// application (client) ID obtained from Azure const string ClientId = "2a9317ca-1111-1111-1111-cb36b901cf64"; // change to your AppId // application's 'client secret' value (application password) const string ClientSecretValue = "ThisIsSomeVerySecretValue"; // change to your secret value // your organization's directory (tenant) ID const string TenantId = "fb561382-2222-2222-2222-06ab992d36b7"; // change to your TenantId // mailbox to access (not an alias) const string SmtpAddress = "someone@example.org"; // change this // default scope of permissions to request static readonly string[] Scopes = new[] { "https://outlook.office365.com/.default", // for accessing Exchange Online with app-only auth };Before your application connects to Office 365's EWS service, it has to request an OAuth 2.0 access token using the Microsoft's authentication API.
using Microsoft.Identity.Client; ... // get an instance of 'confidential client application' API var cca = ConfidentialClientApplicationBuilder .Create(ClientId) .WithClientSecret(ClientSecretValue) .WithTenantId(TenantId) .Build(); // acquire OAuth 2.0 access token from Microsoft 365 AuthenticationResult result = await cca.AcquireTokenForClient(Scopes).ExecuteAsync(); string accessToken = result.AccessToken;Then, connect to
outlook.office365.comusing Rebex EWS package and use the acquired token to start accessing your organization's mailboxes.using Rebex.Net; ... // connect to Office 365 var client = new Ews(); client.Connect("outlook.office365.com", SslMode.Implicit); // specify mailbox to access client.Settings.Impersonation = new EwsImpersonation() { SmtpAddress = SmtpAddress }; // authenticate using the access token client.Login(accessToken, EwsAuthentication.OAuth20); // start working with the mailbox ...To give this a try before adding the code to your application, try our EwsOAuthAppOnlyConsole sample.
Any issues?
Use an up-to-date version of Rebex EWS or Rebex Mail Pack. Old versions of Mail Pack have not been tested with contemporary Exchange Online. They might still work, but if you encounter any issues, please try the latest release.
This guide is only suitable for EWS. For IMAP/POP3 guide, see Office 365 and IMAP or POP3 with OAuth 2.0.
Microsoft 365 does not support app-only authentication for SMTP yet. However, it will still be possible to enable username/password authentication for SMTP after October 1st 2022. Alternatively, it's possible to use EWS to send e-mail as well.
Need help? Ask at Rebex Q&A Forum.