Beware pressing Cancel on Windows Firewall Security Alert
One would think that pressing “Cancel” has no effect and it just closes a window. Unfortunately, there is a side effect in Windows Firewall Security Alert window.
Assume having some application that requires allowing an access through Windows Firewall.
NOTE: For this blog post, we use a small application “ActiveFtpSample”. It connects to an FTP server in “active mode” since this mode requires a connection from server to client (see more about active and passive FTP > mode). Source code of this application is written bellow in this text.
If Windows Firewall first catches the network communication, following window is displayed:
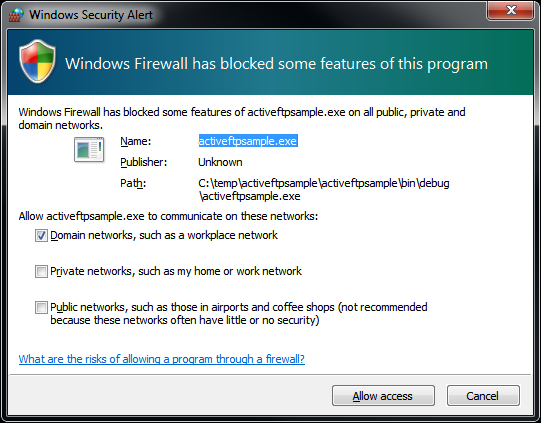
When confirming this dialog by clicking the “Allow access” button, several inbound rules are created in Windows Firewall:
NOTE: to reach the firewall rules, open “Start Menu / Administrative > Tools / Windows Firewall with Advanced Security” and then choose “Inbound rules” from its navigation tree.
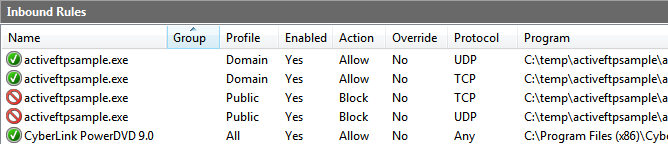
“Allow” rules have been created for “Domain networks” (since the “Domain networks” option has been checked) and “Block” rules have been created for “Public networks”. This is clear, it is exactly what an user may expect when clicking on the “Allow access” button.
However, if the user doesn’t want to deal with this dialog now and closes it by clicking the “Cancel” button, only “Block” rules are created even for the most privileged “Domain” profile:
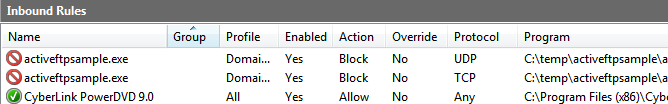
And what’s the hidden pain?
Once the block rules are created in Windows Firewall, the “Windows Security Alert” will be never shown again for this application. If an user cancels the dialog by mistake, the application will keep failing on network communication again and again without any alert at all.
The solution is to delete the “Block” rules in the Windows Firewall configuration. It seems clear now, but it would make troubles if user didn’t notice, that some firewall rules were created.
Sample application
Here is a C # code of sample application, which invokes creating inbound rules in Windows Firewall.
using System;
using Rebex.Net;
namespace ActiveFtpSample
{
class Program
{
static void Main(string[] args)
{
// create FTP client using active FTP transfers
var client = new Ftp();
client.Passive = false;
// connect and login
client.Connect("hostname");
client.Login("username", "password");
// perform some operation to generate FTP traffic
// to be caught by the Windows Firewall
client.GetList();
client.Disconnect();
}
}
}
This application uses the Rebex FTP/SSL component – you should add references to following DLL libraries:
- Rebex.Common.dll
- Rebex.Networking.dll
- Rebex.Ftp.dll
Trial version of the libraries can be downloaded from here.
NOTE: when creating a Windows Forms application, be sure to set the AssemblyTitle attribute (accessible also by properties of Visual Studio project). Value of the AssemblyTitle attribute is put into the “Name” column in Windows Firewall rules. If the AssemblyTitle attribute is omitted, a firewall rule with an empty name is created.